Intune – MEM – Configure Edge browser for iOS and Android

Introduction
It’s Time to Move to EDGE Mobile!
Step 1 App Protection Policies Target Edge for iOS and Android
Step 2 App configuration polices – Target Edge for iOS and Android
Step 3 Check out new Browser experience with EDGE
Documentation
Its_Time_to_Move_to_EDGE_Mobile
Back in November 2019 the Managed browser was announced to be retired March 31 2020. Already from February 1, 2020, the Intune Managed Application was going to removed from Google Play Store and iOS App Store. Since March is right around the corner, it’s about time to get prepared to do the switch.
Regarding a smooth transition, Microsoft let us use all the same Browser Config settings like “com.microsoft.intune.mam.managedbrowser”, so basically we just need to target the Edge for iOS and Android with the existing MAM Policies (app protection and app configuration settings).
With this blog post, I will cover the steps to get started and deep into the browser experience. And In my particular case, I’m going to use EDGE iOS as a corporate browser with some specific settings, just to show the user browser experience. We are also checking the custom settings like “Single sign-on”, Bookmarks and Blocking some specific sites from both end-user and MEM side.
Settings:
- [Specify allowed or blocked sites list for Microsoft Edge][1]
- [Configure managed bookmarks for Microsoft Edge][2]
- [Transition users to their personal context when trying to access a blocked site][3]
Step 1 ) App Protection Policies – Target Edge for iOS and Android
To get started we need to look into the existing App protection Policy.
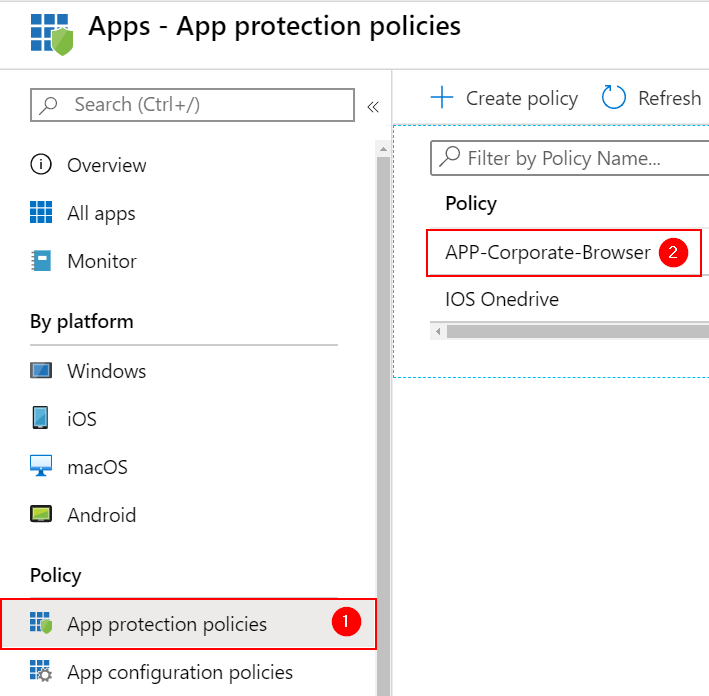
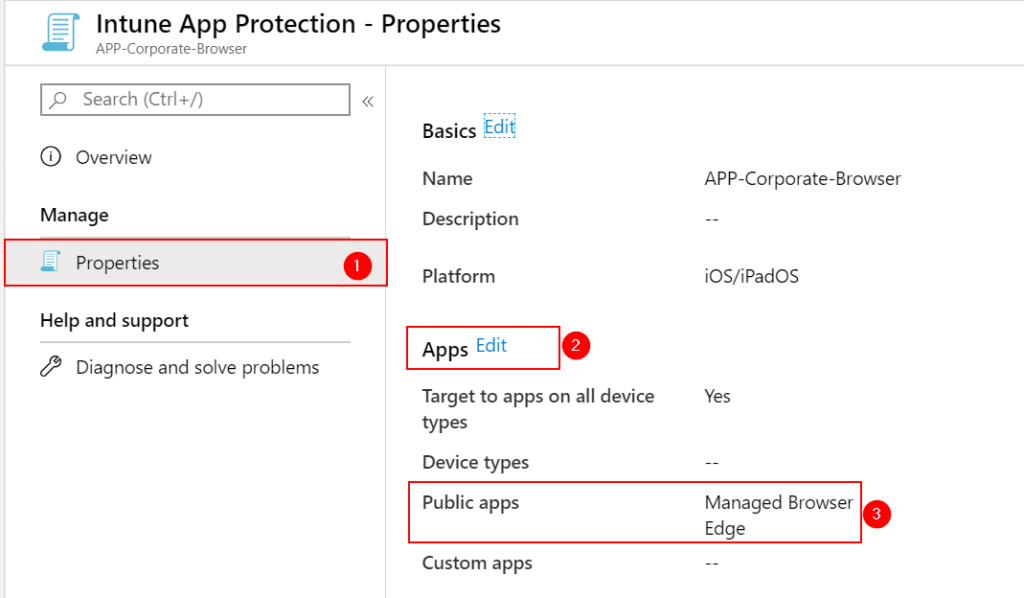
Add EDGE to your Policy under Apps –> Edit and choose EDGE as a Public App (I’m Adding both iOS and Android).
Step 2) App configuration polices – Target Edge for iOS and Android
Change the App configuration polices for your particular configuration.
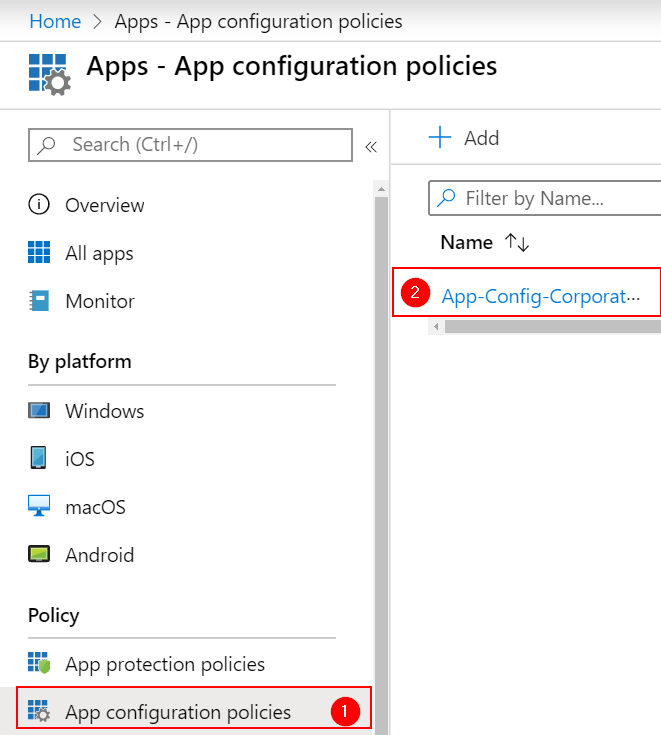
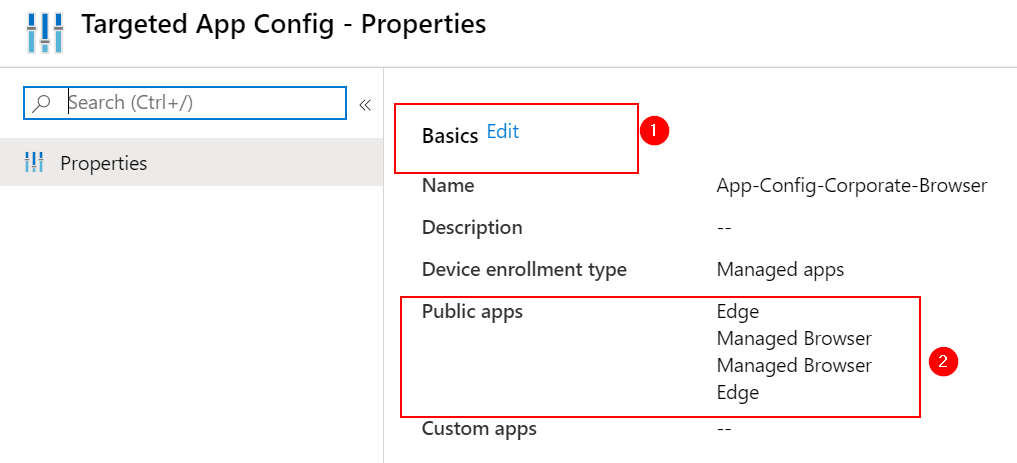
Add EDGE to your Policy under Basics –> Edit and choose EDGE as a Public App (I’m Adding both iOS and Android).
Step 3 ) Check out new Browser experience with EDGE
After adding the EDGE Application to the Policy, we can see that we now have a new layout. All settings have been merged to the “EDGE Configuration Settings” where the “com.microsoft.intune.mam.managedbrowser” is in the new view. You can see that is much easier to change settings without knowing all the “com.microsoft.intune.mam.managedbrowser” settings. We also have new settings like Import and Export either Blocked URLs which is a welcome addition.
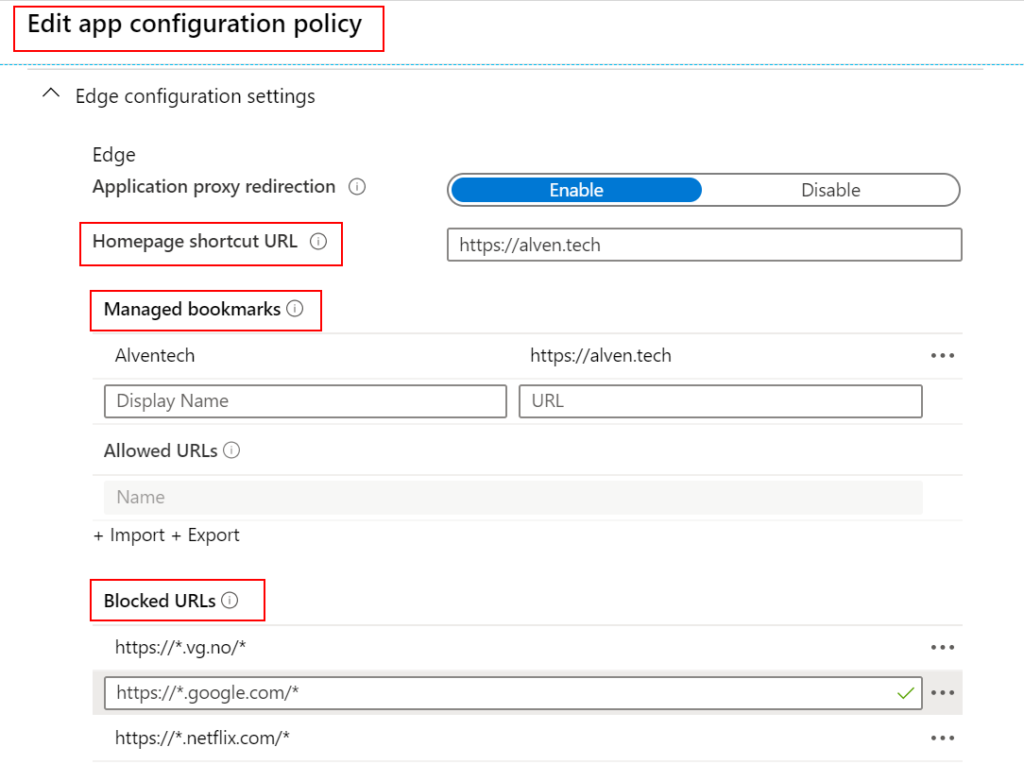
In the video below you can see how the MAM policy is applied and how the browser experience looks when MAM configurations are applied.
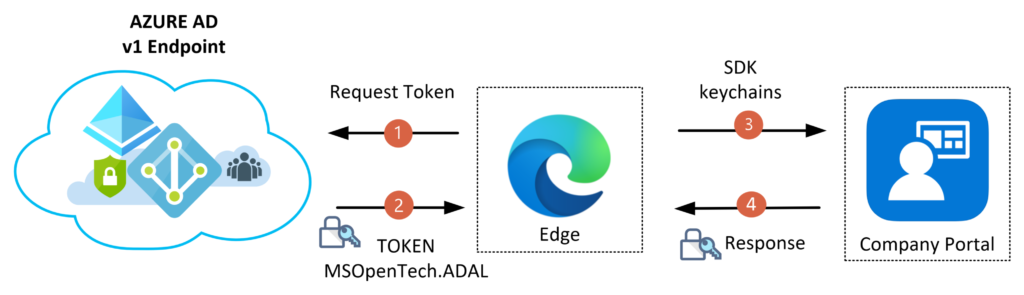
How does “Single sign-on” work on EDGE with iOS?
I have not found any documentation regarding how the “Single Sign-on” Flow works. So to find how “SSO” was working with iOS, I had to dig into the EDGE browser [logs][4]. In the logs, I could find that EDGE is using Cross-app/ keychain sharing with Company Portal, and the SSO” flow is using ADAL – Azure AD v1.0 endpoint. So regarding the authorization flow, the Company Portal already has a valid Authorization Token, and the next request against Azure AD v1.0 endpoint will use the same Application ID. The EDGE Application has another redirect URI than the Company Portal application, but keychain sharing is part of the SDK, so it will use ADAL token. The figure below illustrates the Authentication Flow from 1 to 4. I’m guessing this will change over time since Microsoft will probably migrate to using MSAL – Azure AD v2.0 endpoint eventually.
Summary
The technical changes regarding adding EDGE as the new shiny browser is lucky for us not much work. The needed work will be to create new guides and information to the End-Users. During the pilot, I found one handy key feature when running both browsers for a period of time is that we can [Direct users to Microsoft Edge instead of the Intune Managed Browser][5] with custom settings.
In terms of new MAM Configuration settings, I hope that we will get some more control like changing the start page, so it automatically starts the browser like it did in the Managed Browser. I could also like that we have more control over the SSO settings so it Automatically starts the Sign-On view right after MAM Policy is applied.